Access Control System: How to Choose the Right Credential Types
Mike Reynolds is the Director of Sales at DGA Security. He has more than 17 years of commercial security experience, and has strong expertise in designing security systems for national accounts and businesses in “high risk” markets. Mike enjoys collaborating with customers, designers and industry trade partners to solve unique business security challenges and create innovative solutions.
When it comes to access credentials, they don't have to be one-type-fits-all. The most common access credential types are access cards, key fobs, tags and mobile-based apps.
You can also use a person’s unique morphological markers such as fingerprints and iris scan as a biometric access credential. Biometric readers are implemented less frequently and are typically used to protect very high security areas.
There are pros and cons associated with each access credential type so we recommend that you choose the type that best meets your security requirements and employee preferences. Remember, modern credential readers can be programmed to simultaneously support multiple credential types.
This article provides an overview of different access credential types and explains their unique benefits, use cases and costs.
High-Security Access Cards and Key Fobs

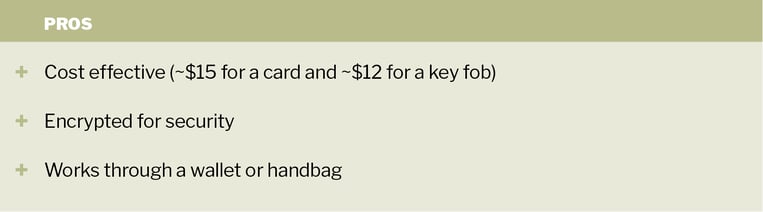
Despite the different form factor, access cards and key fobs work identically. They are often called Proximity Cards or Prox Cards because they can be read when they come in close proximity with the reader without requiring direct contact.
However, not all proximity cards or fobs are created equal. What sets them apart, and increases the per unit cost, is the level of encryption they provide.
The older access cards and fobs use low frequency RFID technology that operates in the 125 KHz range. Because the ID number stored in the card or fob is not encrypted, it can be intercepted and cloned by a hacker who walks nearby the cardholder with a generic RFID reader.
Therefore, we always recommend high-frequency, high-security RFID cards and fobs that use encryption. Think of encryption as a complex mathematical lock and key that creates a unique bi-directional “handshake” between the card and the reader before the ID number can be read. This bi-directional authentication process makes it extremely difficult for hackers to compromise these systems.
You should expect to pay around $15 for a high-security access card and around $12 for a high-security key fob. These are extremely popular among our customers because they are highly secure, cost effective and easy to manage.
High-Security Tags

High-security tags have the shape of a small, round sticker but work the same way as the high-security RFID access cards and key fobs. Tags are particularly useful for businesses located inside a multi-tenant building with a separate building entry system. Instead of carrying two access cards — one for the building and one for the office — an employee can simply attach the tag to the back of their building entry card.
If the tag and the building entry card both use a similar radio frequency, they may not work properly. Therefore, it is important to test for potential interference before selecting this option.

Mobile Access Credential

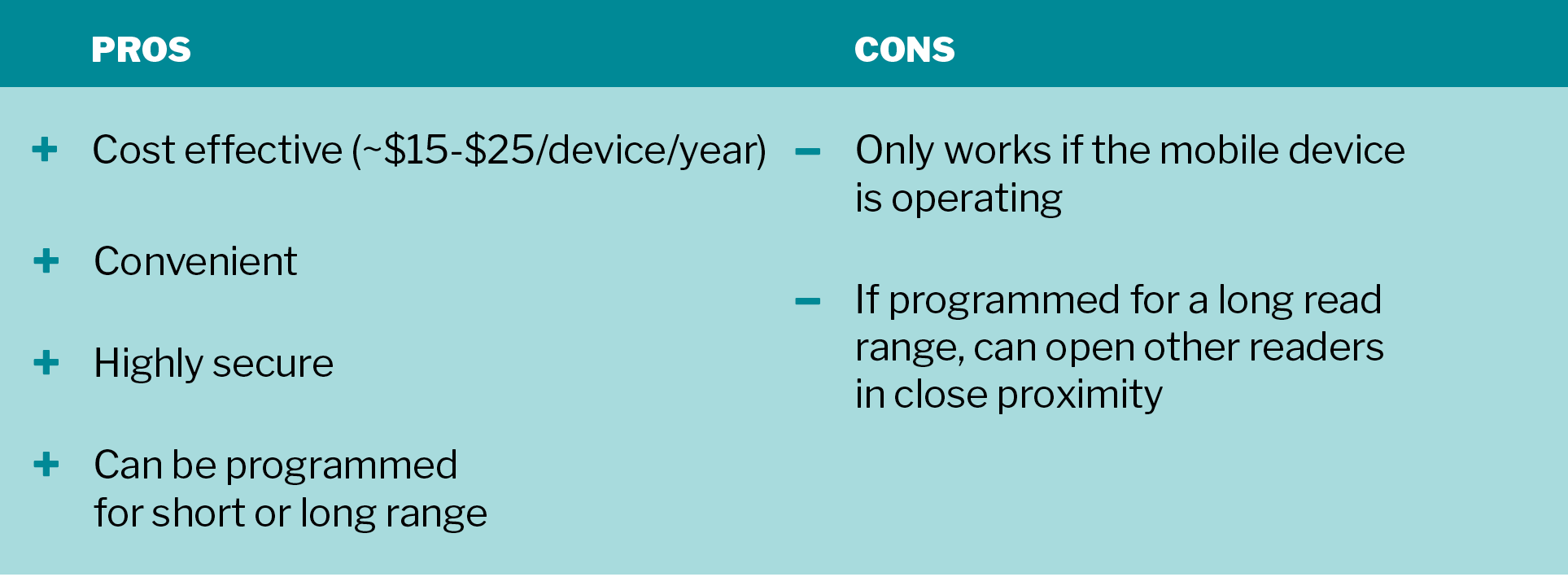
Mobile access credentials are rapidly gaining traction because more and more employees prefer the convenience of using their mobile phones for just about everything. Mobile access credential can use Near Field Communication (NFC) or Bluetooth connection to communicate between the phone and the reader. More specifically, mobile access credentials use a type of Bluetooth technology called BLE (Bluetooth Low Energy) that consumes significantly less power from your mobile device by remaining in a sleep mode unless a connection is initiated.
While we offer both NFC and BLE-enabled mobile access control options, the BLE option is more popular because it can be programmed for both short and long read ranges (e.g., a six foot read range for a parking garage entrance).
Setting up a mobile access credential is simple. A user downloads and authenticates the mobile app using a link emailed by the system administrator. As long as the app is running in the background, the user can open the door with a tap (for the NFC and BLE options) or a slight twist motion of the phone (for the BLE option only).
Both NFC and BLE-based mobile access credentials are highly secure, cost effective and convenient. But they are not without a couple of hiccups. For one, if your phone runs out of battery, your mobile access credential will not work. That’s why many of our customers who opt for a mobile access credential also have a back-up access card. Additionally, a BLE mobile access credential programmed for a long read range can inadvertently open other protected doors in close proximity.
Biometric Readers

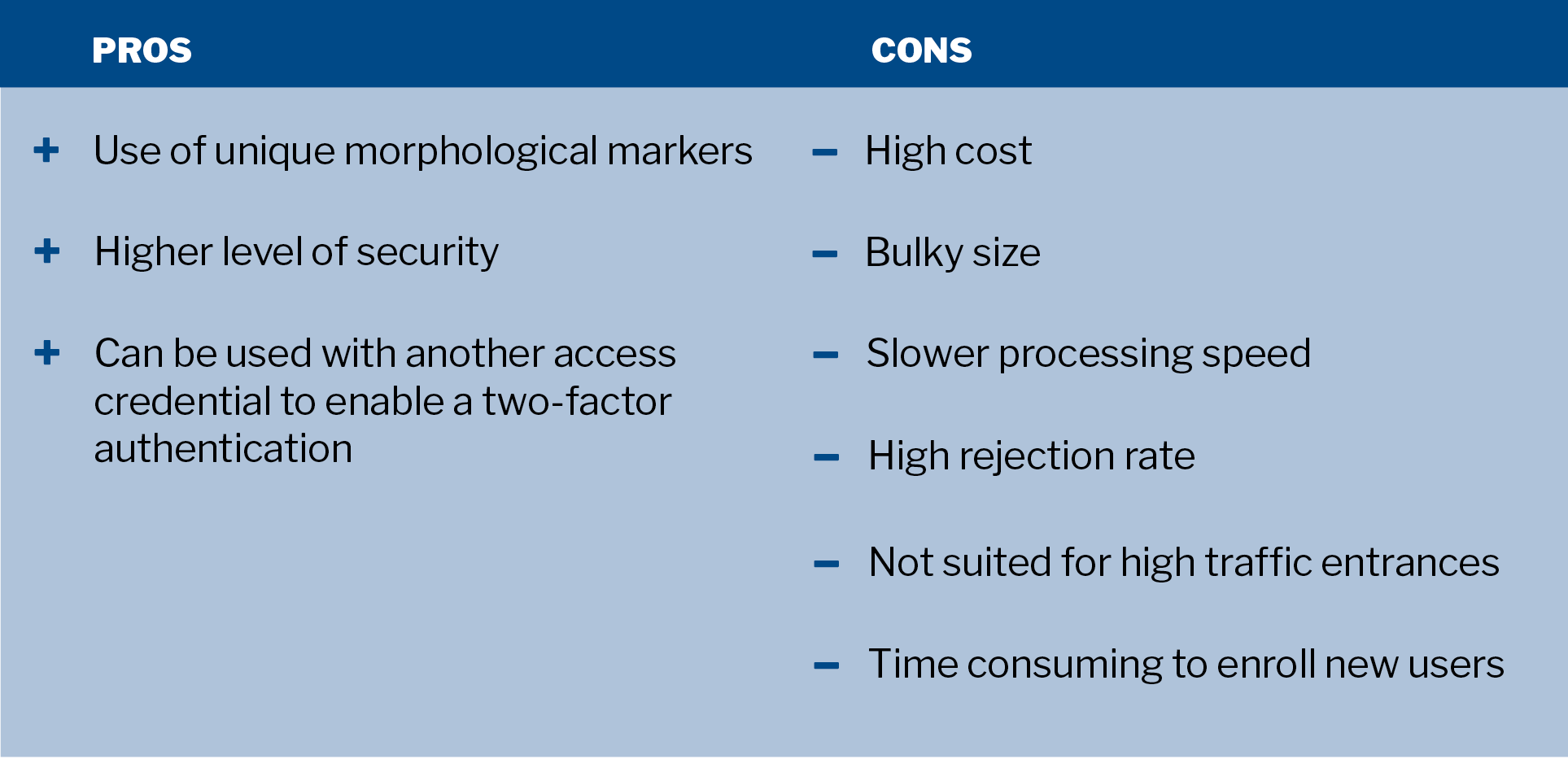
Biometric readers rely on unique morphological characteristics associated with a person to grant access. Fingerprint and palm readers are the most popular, but biometric readers can also scan a person’s iris, voice or face. Biometric readers can also be deployed in combination with other access credentials (e.g., PIN pads, access cards) to enable a two-factor authentication.
In theory, biometric readers offer the highest level of security of all the access credential options. But in practice, biometric readers are not yet widely adopted in physical access control due to their size, cost, speed and high rejection rate. Due to its slower processing speed and high rejection rate, biometric readers are not suited for high traffic entrances. Registering new users is more time consuming than other credential types since every authorized user needs to be physically enrolled for the biometric reader on site.
A high quality fingerprint reader will cost in the thousands, not including the separate server likely needed on location to operate the reader.
Key Takeaways
Each access credential type has a unique set of advantages and disadvantages so it pays to evaluate different credential types against your business's unique security requirements and employee preferences. Remember, you don't have to choose just one type of access credential for your business. Modern credential readers can be programmed to simultaneously support cards, fobs, tags or mobile credentials.
Got questions about business security cameras? We’ve got answers.
DGA has been specializing in commercial security and fire systems for more than 50 years. Call us for a free consultation at 800-PICK-DGA (800-742-5342) or submit a request online.
Related Articles
How a Network Outage Impacts Cloud-Based Access Control Systems
Should your business security systems provider have a SOC audit?
Access Control: What are the First Person In and DoorStat Features?




